Software-Defined Networking (SDN) is a network architecture approach that enables the network to be intelligently and centrally controlled, or 'programmed,' using software applications.
TYPES OF SDN ATTACK
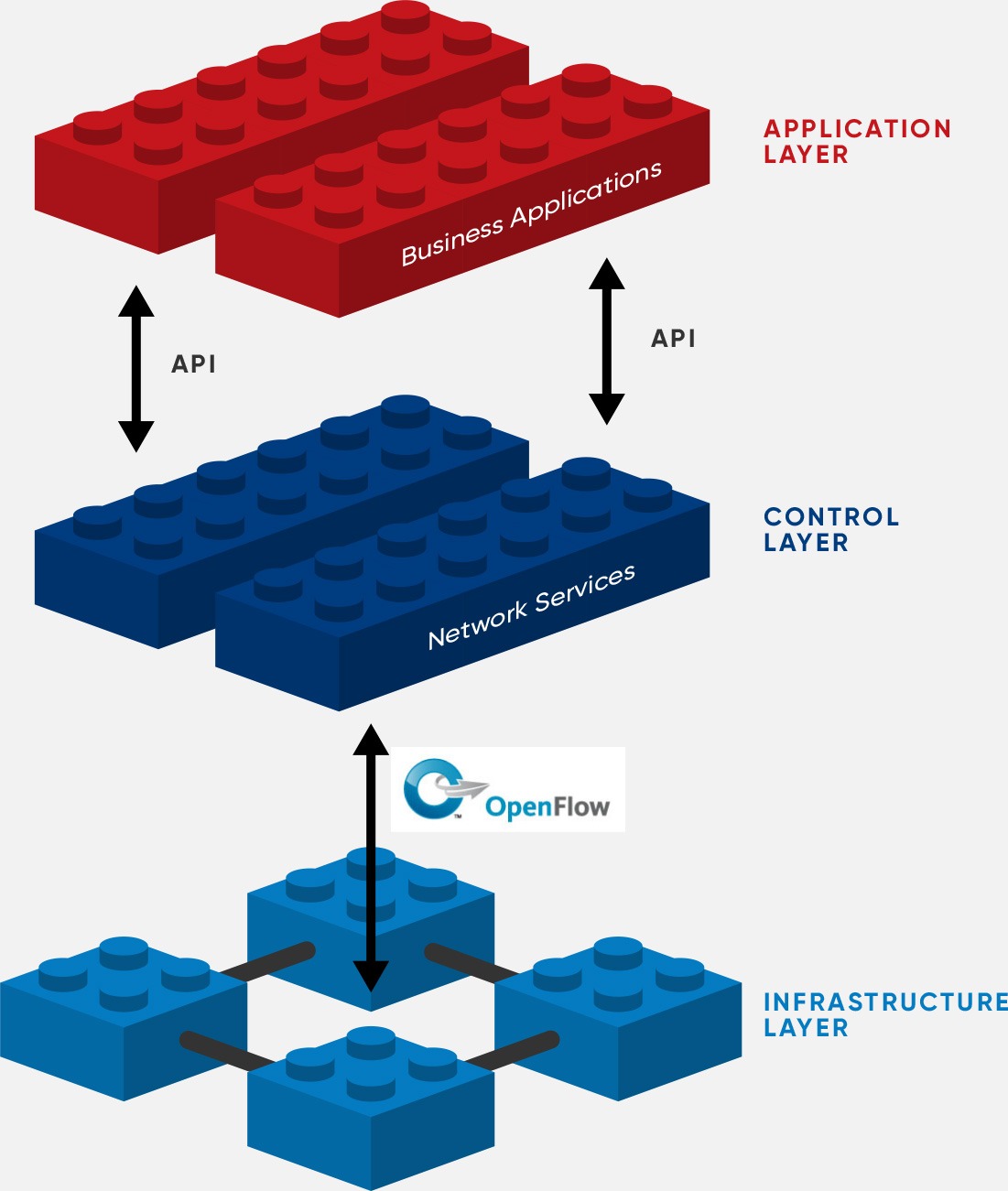
1. Attacks at Data Plane Layer
Attackers could target the network elements from within the network itself. An attacker could theoretically gain unauthorized physical or virtual access to the network or compromise a host that is already connected to the SDN and then try to perform attacks to destabilize the network elements. This could be a type of Denial of Service (DoS) attack or it could be a type of fuzzing attack to try to attack the network elements.
There are numerous southbound APIs and protocols used for the controller to communicate with the network elements. These SDN southbound communications could use OpenFlow (OF), Open vSwitch Database Management Protocol (OVSDB), Path Computation Element Communication Protocol (PCEP), Interface to the Routing System (I2RS), BGP-LS, OpenStack Neutron, Open Management Infrastructure (OMI), Puppet, Chef, Diameter, Radius, NETCONF, Extensible Messaging and Presence Protocol (XMPP), Locator/ID Separation Protocol (LISP), Simple Network Management Protocol (SNMP), CLI, Embedded Event Manager (EEM), Cisco onePK, Application Centric Infrastructure (ACI), Opflex, among others. Each of these protocols has their own methods of securing the communications to network elements. However, many of these protocols are very new and implementers may not have set them up in the most secure way possible.
An attacker could also leverage these protocols and attempt to instantiate new flows into the device’s flow-table. The attacker would want to try to spoof new flows to permit specific types of traffic that should be disallowed across the network. If an attacker could create a flow that bypasses the traffic steering that guides traffic through a firewall the attacker would have a decided advantage. If the attacker can steer traffic in their direction, they may try to leverage that capability to sniff traffic and perform a Man in the Middle (MITM) attack.An attacker would like to eavesdrop on flows to see what flows are in use and what traffic is being permitted across the network. The attacker would want to try to eavesdrop on southbound communication between the network element and the controller. This information could be useful for a replay attack or simply for reconnaissance purposes.
Many SDN systems are deployed within data centers and data centers are more frequently using Data Center Interconnect (DCI) protocols such as Network Virtualization using Generic Routing Encapsulation (NVGRE), Stateless Transport Tunneling (STT), Virtual Extensible LAN (VXLAN), Cisco Overlay Transport Virtualization (OTV), Layer 2 Multi-Path (L2MP), TRILL-based protocols (Cisco FabricPath, Juniper QFabric, Brocade VCS Fabric), Shortest Path Bridging (SPB), among others. These protocols may lack authentication and any form of encryption to secure the packet contents. These new protocols could possess vulnerabilities due to an aspect of the protocol design or the way the vendor or customer has implemented the protocol. An attacker could be motivated to create spoofed traffic in such a way that it traverses the DCI links or to create a DoS attack of the DCI connections.
2. Attacks at Controller Layer
It is obvious that the SDN controller is an attack target. An attacker would try to target the SDN controller for several purposes. The attacker would want to instantiate new flows by either spoofing northbound API messages or spoofing southbound messages toward the network devices. If an attacker can successfully spoof flows from the legitimate controller then the attacker would have the ability to allow traffic to flow across the SDN at their will and possibly bypass policies that may be relied on for security.
An attacker might try to perform a DoS of the controller or use another method to cause the controller to fail. The attacker might try to attempt some form of resource consumption attack on the controller to bog it down and cause it to respond extremely slowly to Packet_In events and make it slow to send Packet_Out messages.
3. Attacks at SDN Layer
Attacking the security of the northbound protocol would also be a likely vector. There are many northbound APIs that are used by SDN controllers. Northbound APIs could use Python, Java, C, REST, XML, JSON, among others. If the attacker could leverage the vulnerable northbound API, then the attacker would have control over the SDN network through the controller. If the controller lacked any form of security for the northbound API, then the attacker might be able to create their own SDN policies and thus gain control of the SDN environment. Often times, there is a default password that is used for a REST API which is trivial to determine. If an SDN deployment didn’t change this default password and the attacker could create packets toward the controller’s management interface, then the attacker could query the configuration of the SDN environment and put in their own configuration.
🍎 TOOLS USED FOR PENTESTING SDN🍎
https://github.com/GAR-Project/project
https://github.com/smythtech/sdnpwn
https://github.com/aswanthpp/Analysis-of-DDoS-Attacks-in-SDN-Environments
https://github.com/JamesQuintero/DDoS-Attack-Detection
https://github.com/alonecoder1337/Dos-Attack-Detection-using-Machine-Learning

إرسال تعليق