Hey Folks, in this tutorial we will show you the whole process of installing and configuring a network scanning tool called “Nexpose“. Nexpose identifies the active services, open ports, and running applications on each machine, and it attempts to find vulnerabilities that may exist based on the attributes of the known services and applications. To get an in-depth knowledge about this tool, you can go here.
Let’s get to the point 
Registration
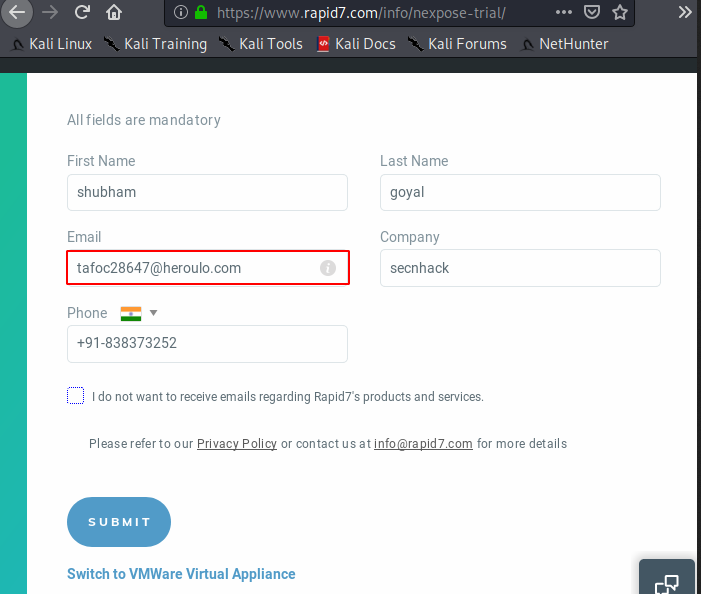
Nexus offers us a 14-day free trial to get to know about this tool much better but you have to register to grab this chance. Usually it supports domain or company email addresses, but you can also use temporary email.
1 | https://www.rapid7.com/info/nexpose-trial/ |
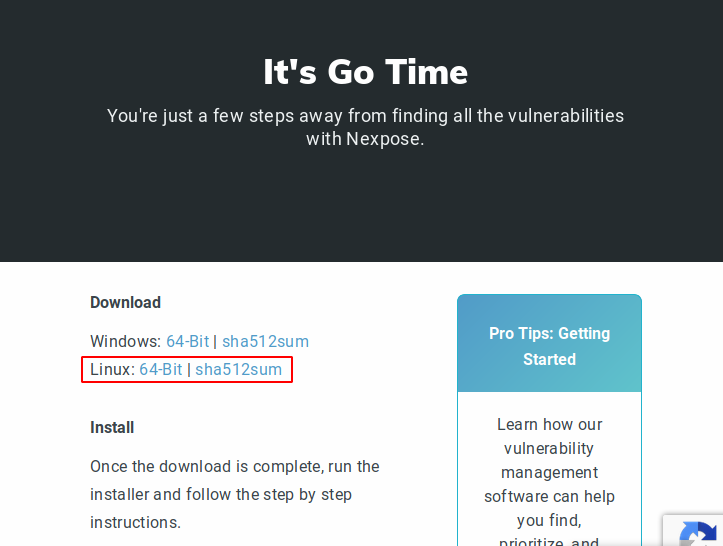
After submitting the details we redirect to the download page from where we download the software for the linux operating system.
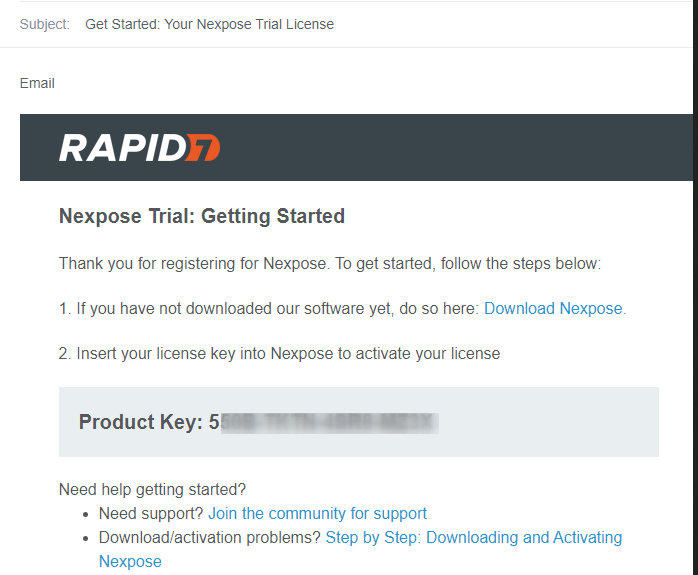
After a few minutes we received the product key at our temporary email address. Hold it tight 
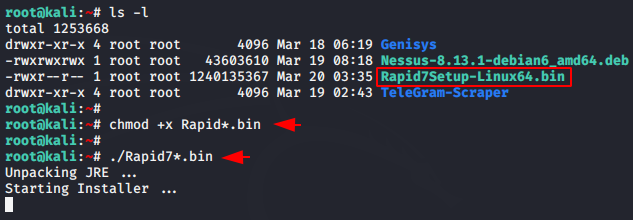
Now we move the downloaded file to our compatible location, allow it executable and start the script.
1 | chmod +x Rapid.bin ./Rapid7.bin |
Hmm 
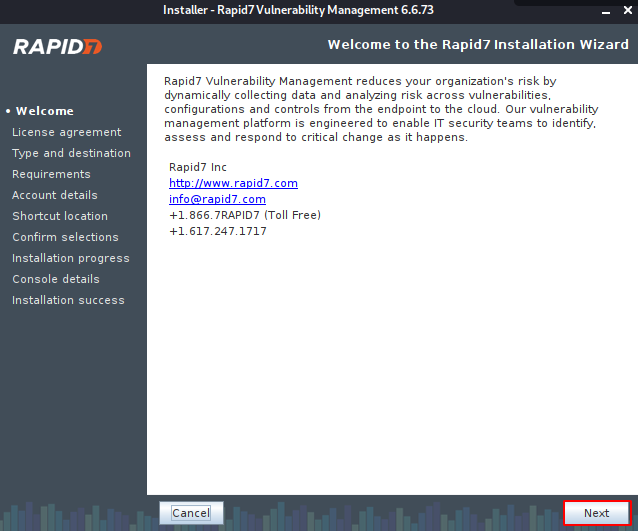
Everything is already set as it should be, so we need to move forward again.
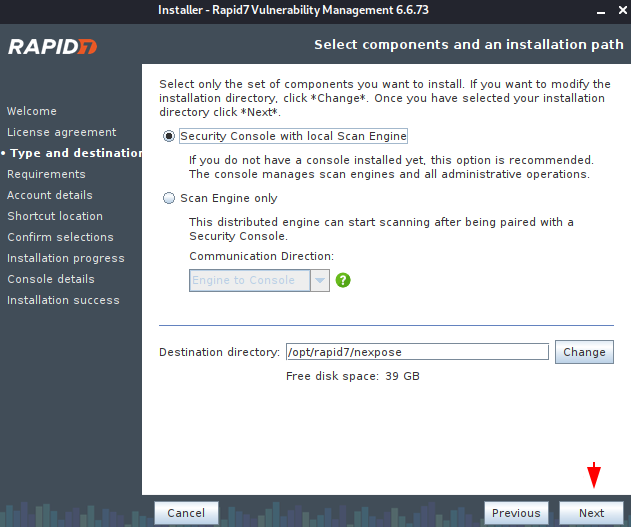
If you want to provide a proxy then it is up to you but in our case we will move forward.
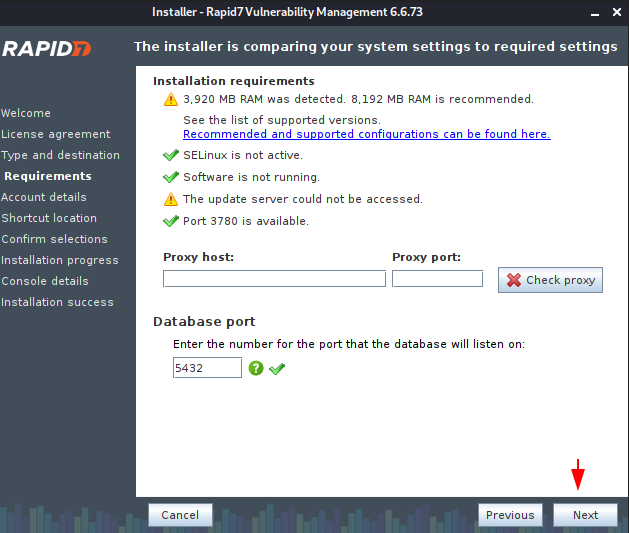
Setting Credentials
We need to keep the username and password to protect the admin console.
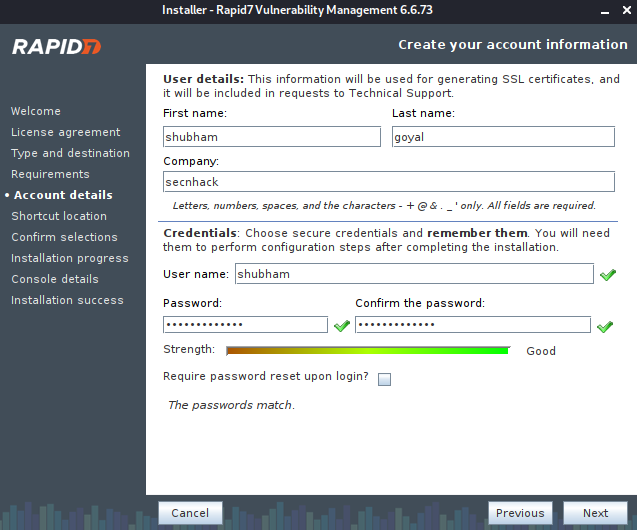
We click on “Initialize and start after installation” and proceed.
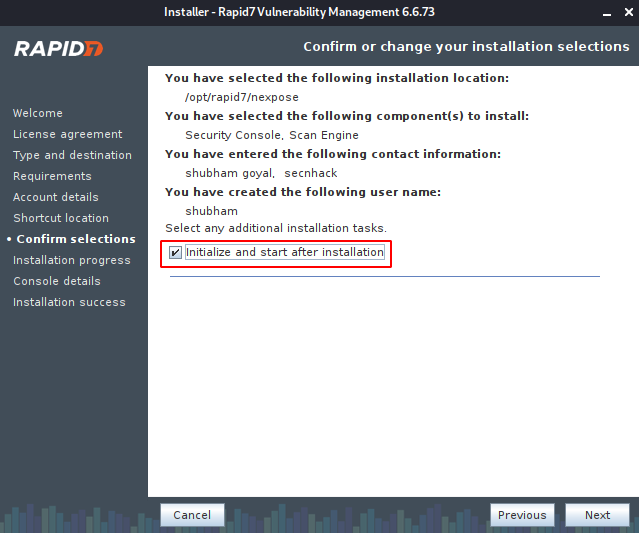
Good 
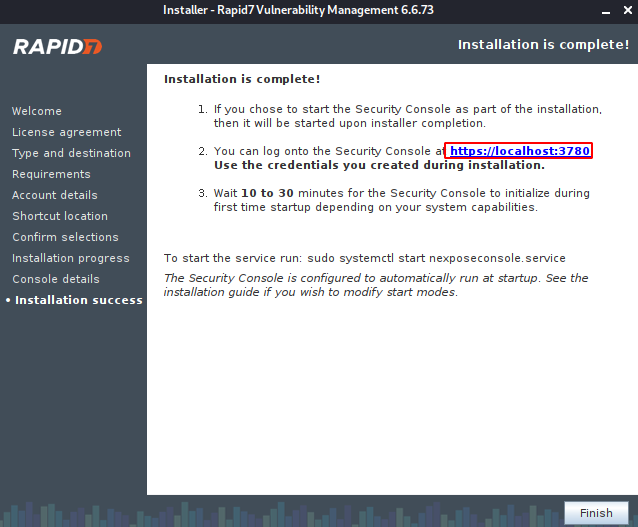
Hmm 
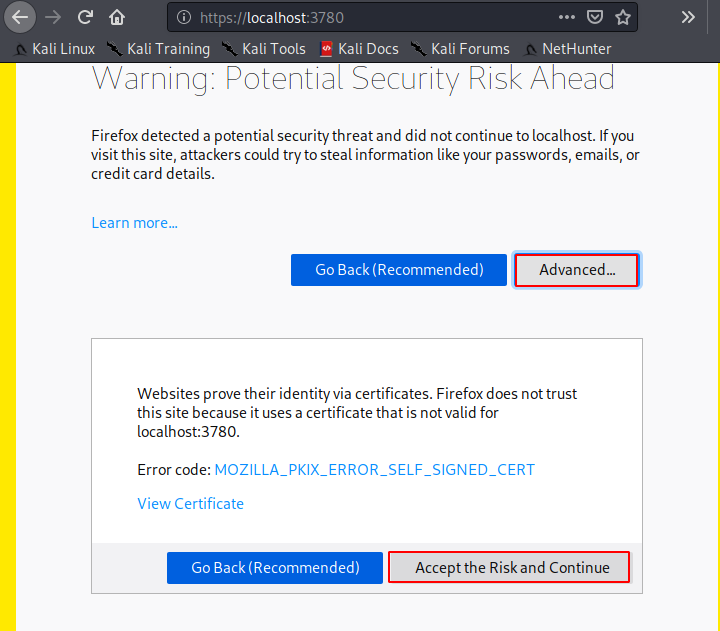
Great 
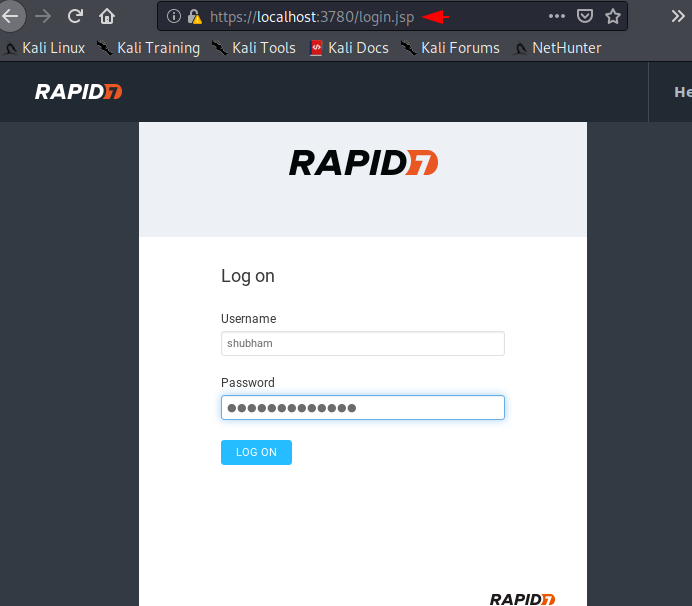
Now here we have to submit the product key which we got earlier by this tool at our email address.
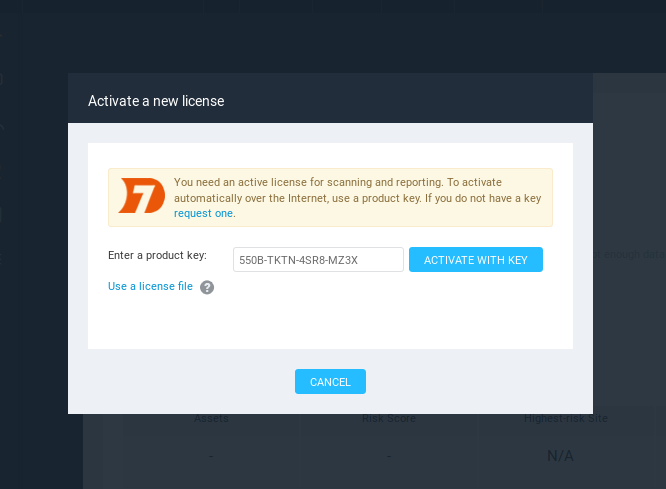
Amazing 

Post a Comment